Vulnerability Summary
A Stored Cross-Site Scripting (XSS) vulnerability exists in version 1.0 of the Expense Management System application by EGavilan Media that allows for arbitrary execution of JavaScript commands.
Stored XSS vulnerabilities enable attackers to store malicious scripts in a target application. These scripts are then served to users who view the stored data, potentially leading to session hijacking, credential theft, or redirection to malicious sites.
CVSS v3.1 Metrics
| Metric | Value |
|---|---|
| Base Score | 5.4 (MEDIUM) |
| Vector | CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N |
Weakness Enumeration
| CWE ID | Description |
|---|---|
| CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) |
Proof of Concept (PoC)
Steps to Reproduce
- Download, install, and run the Expense Management System application (version 1.0).
- Navigate to:
http://localhost/index.php - Click on Add Expense and fill out the form as follows:
- Description:
<script>alert(document.cookie);</script> - Amount: any numeric value
- Date: any valid date
- Description:
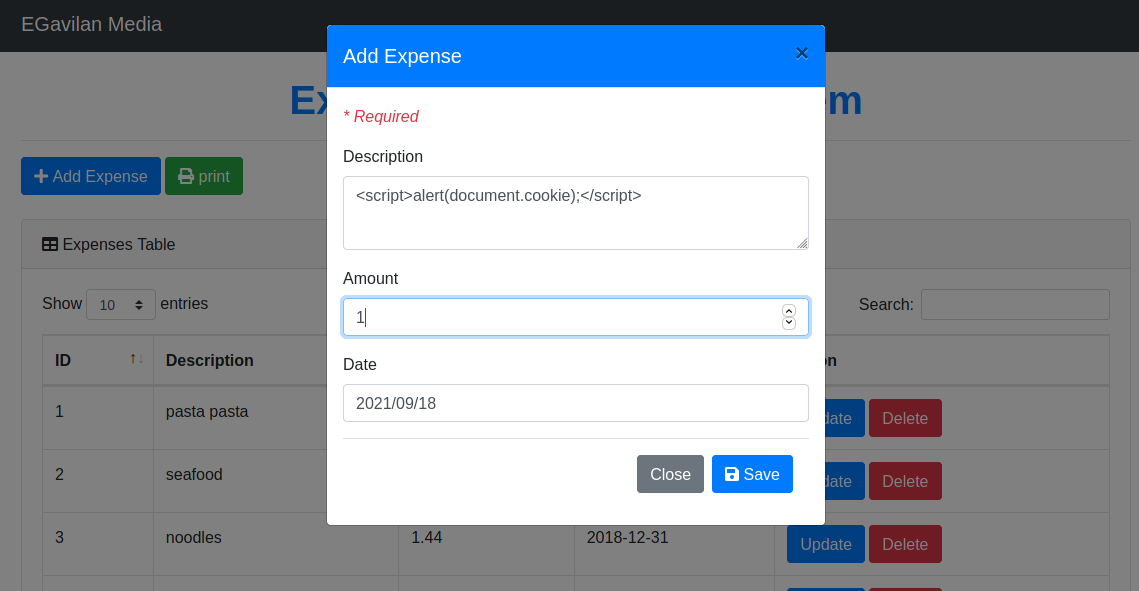
- Press the Save button.
- Navigate to the page displaying the newly added expense.
- The JavaScript payload will execute from the description field.
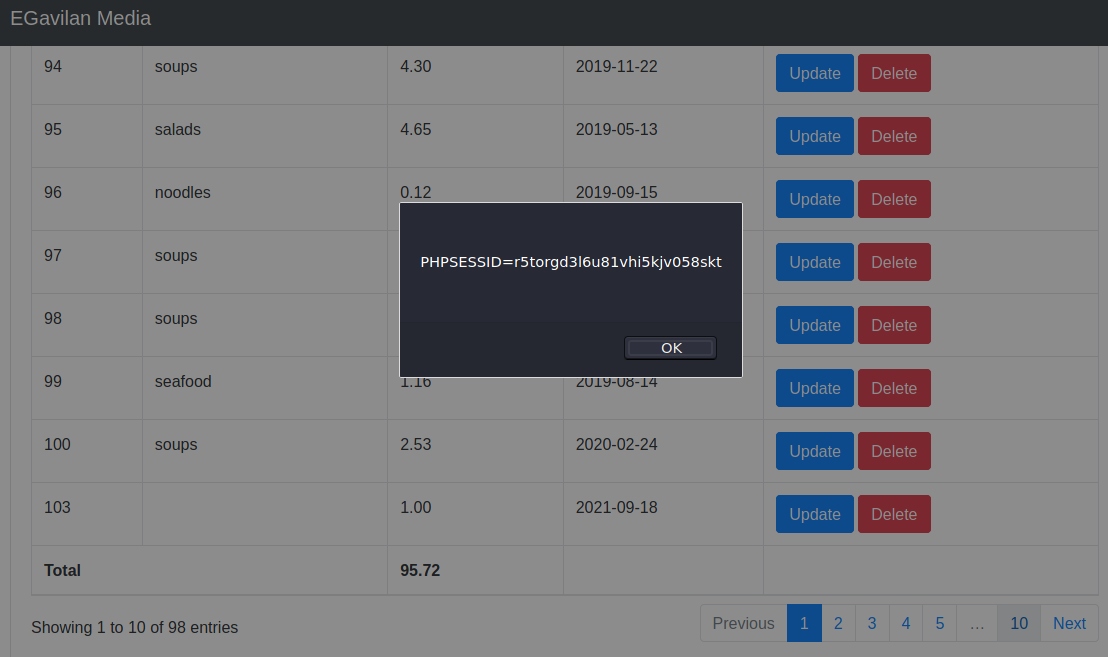
Suggested Mitigations
- Properly encode all dynamic content before rendering in HTML.
- Sanitize user inputs server-side using am HTML sanitization library.
- Implement Content Security Policy (CSP) headers to mitigate script injection.