Vulnerability Summary
A Stored Cross-Site Scripting (XSS) vulnerability exists in version 1.2.1 of the FlatPress application. This vulnerability allows an authenticated attacker to inject malicious JavaScript code into blog content, which will execute in the context of any user visiting the affected page.
Stored XSS occurs when user-supplied input is stored on the server (e.g., in a database or file system) and later rendered in a web page without proper encoding or sanitization. This can lead to session hijacking, defacement, or redirection to malicious sites.
CVSS v3.1 Metrics
| Metric | Value |
|---|---|
| Base Score | 5.4 (MEDIUM) |
| Vector | CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N |
Weakness Enumeration
| CWE ID | Description |
|---|---|
| CWE-79 | Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) |
Proof of Concept (PoC)
Steps to Reproduce
- Log in to the FlatPress administration area.
- Navigate to Entries → Write Entry.
- Enter any value in the Subject field.
- In the Content area, insert the following payload:
<script>alert(document.cookie)</script>
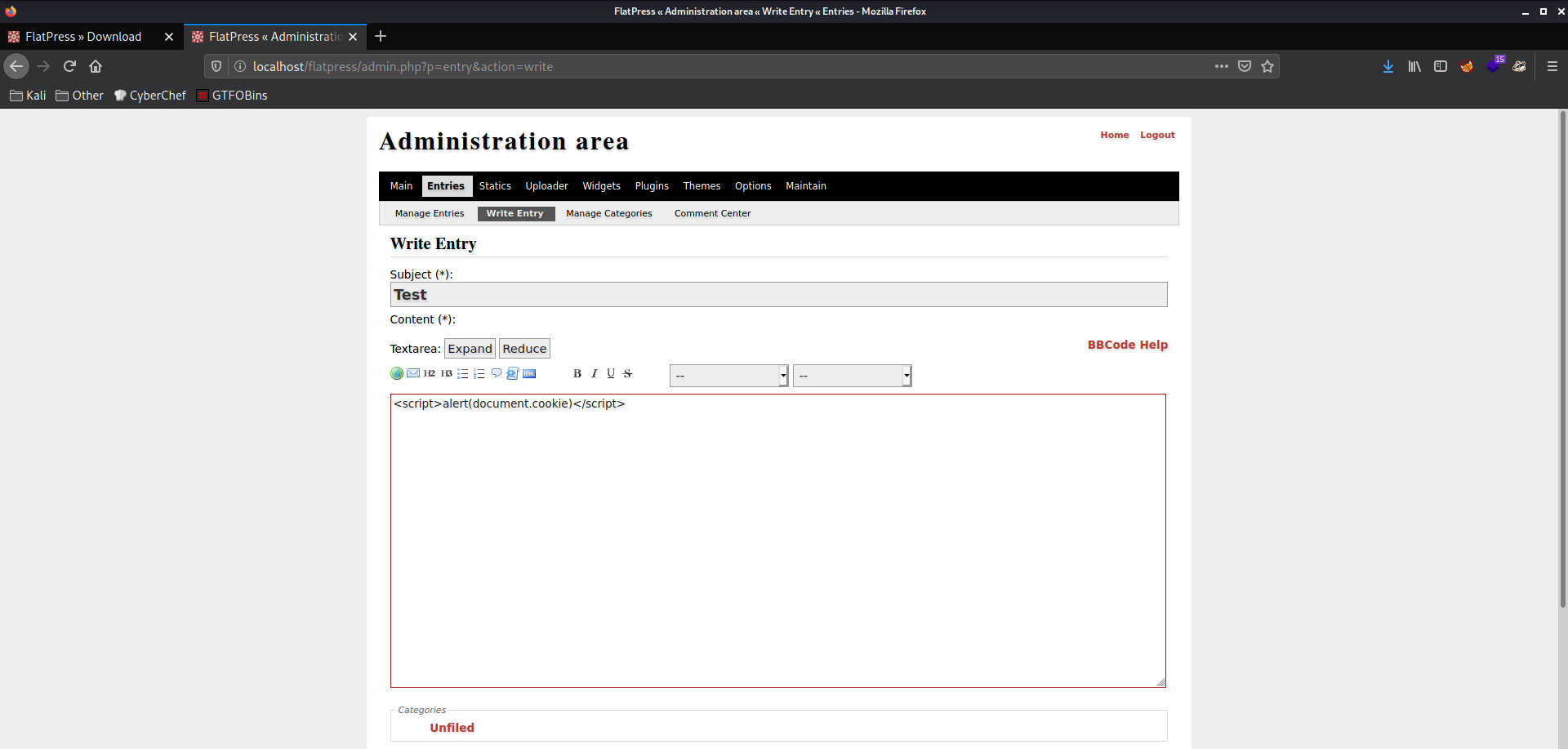
- Click the Save & Continue button.
- The stored XSS payload is now saved and will be executed whenever the post is viewed.
- Navigate to the FlatPress homepage to verify the execution of the payload.
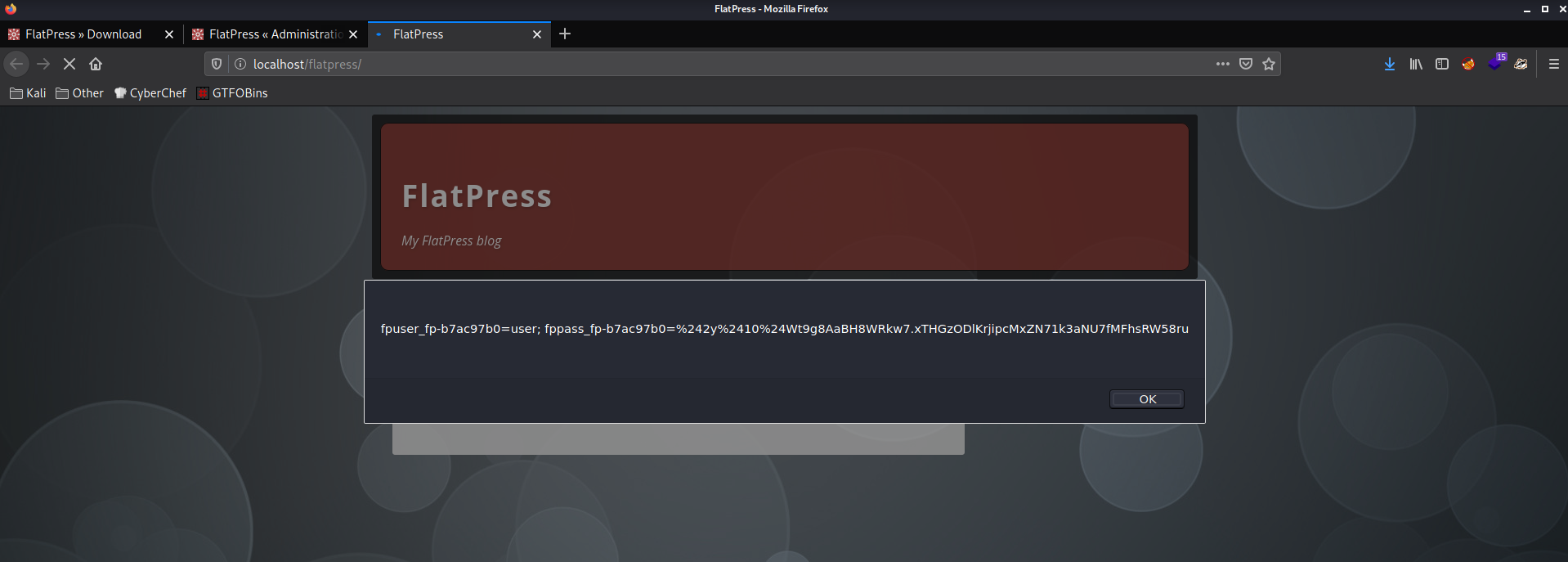
Suggested Mitigations
- Properly encode all dynamic content before rendering in HTML.
- Sanitize user inputs server-side using am HTML sanitization library.
- Implement Content Security Policy (CSP) headers to mitigate script injection.