Vulnerability Summary
A SQL injection vulnerability in the Content Management System provided by GRANDCOM, s.r.o., version 4.2 and older, allows remote unauthenticated attackers to bypass authentication via a crafted username during a login attempt. Any unauthorized user with access to the application is able to exploit this vulnerability.
A SQL Injection attack consists of inserting an SQL query through input data from the client into the application. Upon successful exploitation, it is possible to retrieve detailed data from the database, edit database data such as inserting, updating, or deleting records, perform administrative operations, or in some cases, execute commands directly on the operating system.
CVSS v3.1 Metrics
| Metric | Value |
|---|---|
| Base Score | 9.8 (CRITICAL) |
| Vector | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H |
Weakness Enumeration
| CWE ID | Description |
|---|---|
| CWE-89 | Improper Neutralization of Special Elements used in an SQL Command (‘SQL Injection’) |
Proof of Concept (PoC)
Steps to Reproduce
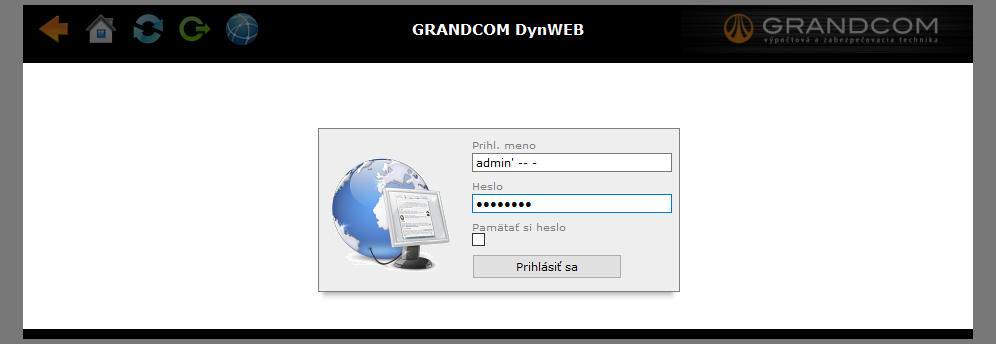
- Visit the following resource:
/admin/index.php - Enter the following credentials:
- Username:
admin' -- - - Password: any value
- Username:
- Press the Login button.
This results in a successful authentication bypass.
Suggested Mitigations
- Use of prepared statements (with parameterized queries).
- Use of stored procedures.
- Allow-list input validation.
- Escape all user-supplied input.